Reviews
Proactive Protection: Safeguarding Your Business in the Digital Age

Imagine getting hit by a cyberattack – one day everything’s fine; the next you’re hemorrhaging money with your good name sullied and lawyers knocking at your door. Firms need a tight grip on cyber defense strategies if they hope to secure private details, maintain consumer faith, and carry on without hitches.
The reason we’ve got to be solid on cybersecurity? Hackers aren’t playing around – they’re constantly finding new ways in. From cunning email scams aiming to phish out sensitive info, down to malicious software seeking cracks in system armor—businesses have got quite the fight keeping these digital foes at bay. Those companies that highly value privacy in the digital age and are willing to invest in cybersecurity are more resilient in the long run and are more likely to withstand all the blows of modern times.
1. Conduct Regular Risk Assessments
To remain at the forefront of cyber security, it’s essential to routinely perform risk assessments. At this core stage, we’re digging into our system’s weak spots and pondering the “what ifs” of a possible security mess-up. Understanding the soft spots in our digital walls is like getting the playbook of an opposing team – it means we can fortify our lines long before any threats come knocking. Regularly evaluating risks does two big things – ensures compliance with specialized standards and demonstrates unwavering dedication to client data protection.
2. Protecting Connections via VPN
In the office, almost all companies have measures in place to secure their connections, but what happens when employees connect to servers remotely? To avoid potential risks, it is better to use a VPN app for Windows. Companies that require employees to download VeePN can protect themselves from phishing, password compromise, spyware, malware infections, and targeted hacking attacks. Moreover, desktop VPN can be protected even when using public Wi-Fi networks. Today, PC VPN is not a luxury, but a necessity, especially since the price is only a few dollars per month.
3. Don’t Overshare on Social Media
Social media platforms may not always clearly communicate the privacy settings available to you. Often, user profiles are set to public by default, with the option to switch them to private buried within the settings.
Once you adjust your profile to private, preventing unknown viewers from accessing your posts, the social networks still monitor your online actions and interactions for data, which is then provided to advertisers. Considering this, it’s wise to be cautious about what you share and engage with on these sites. Being mindful of your activity is a crucial step towards ensuring your safety and protecting any personal or sensitive information.
4. Implement Multifactor Authentication
Multifactor authentication (MFA) offers a straightforward but powerful method for enhancing the security of your systems. By implementing MFA, individuals must supply at least two forms of verification to access a particular resource. This could be a combination of a password and a unique code sent to their mobile device. Such an approach greatly diminishes the likelihood of unauthorized entries, safeguarding your system even in the event of a password breach. For optimum security against the theft of credentials, it’s advisable to incorporate MFA across all essential business applications and services.
5. Establish Standard Practices
Employees must be equipped not just with a broad understanding of cybersecurity principles but also with clear instructions for responding to cybersecurity incidents. Such guidelines are crucial for preventing and minimizing the impact of security breaches and dictating the immediate steps to take should one occur.
It’s equally important to define and enforce data access policies within the organization. If you require the use of VPN on Firefox, then this should be stated in the rules, and not just said in words. This applies to all rules. Granting unrestricted access to every member of the company poses a significant risk and is generally unwarranted. By restricting access solely to those with a legitimate need, the organization can address a substantial number of its data privacy issues effectively.

6. Limit Сollection Data
Companies often fall into the trap of collecting too much information—akin to oversharing. Accumulating excessive data increases the risk to your business. It’s crucial to evaluate the necessity of each piece of data you collect.
Protecting personally identifiable information (PII) is a company’s responsibility. Exposure of this data can lead to significant consequences, including the requirement for the company to provide compensation to those affected. However, limiting data collection to essentials like first names and emails can minimize both the risk and potential losses from data exposure.
7. Invest in Employee Training and Awareness
The primary factor behind most security violations? Human mistakes. Team members may inadvertently engage with phishing schemes or opt for insufficiently secure passwords, thereby exposing your company to danger. By allocating resources to consistent education, you can empower your workforce to grasp the critical nature of cybersecurity. This includes teaching them to identify and steer clear of potential hazards.
Summing Up
Assuming that you’re shielded from data breaches is a risky stance. Recognizing the possibility of exposure—even when you’ve done nothing wrong—prompts proactive measures for protection. This article provides essential tips to help maintain your online security, whether you’re running a business or navigating the digital world as an individual.

-
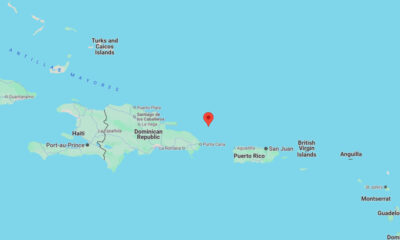
 US News1 week ago
US News1 week agoMagnitude 5.7 earthquake strikes between Dominican Republic and Puerto Rico
-

 Legal2 days ago
Legal2 days agoFirefighters ambushed while responding to Idaho wildfire, at least 2 killed
-
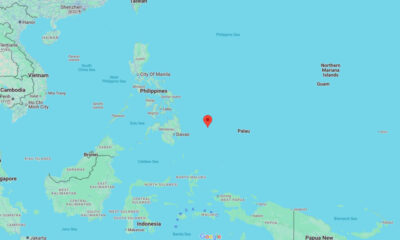
 World1 week ago
World1 week agoMagnitude 6.3 earthquake strikes offshore the Philippines
-

 US News5 days ago
US News5 days agoSmall meteorite fragment may have struck Georgia home
-

 Legal5 days ago
Legal5 days agoArmed woman blocks traffic on freeway in Houston, Texas
-

 Legal4 days ago
Legal4 days agoWashington Post journalist Thomas LeGro arrested for child porn possession
-

 Legal1 week ago
Legal1 week agoNo threat found after vehicle investigated near White House
-

 US News1 week ago
US News1 week agoIran warned of sleeper-cell terror in U.S. before nuclear strikes – NBC News




