Reviews
Why Security Professionals Should Consider Risk Beyond Code

When we think of cybersecurity, code is often the first thing that comes to mind. Vulnerabilities hidden in software, flaws in encryption, or mistakes in development practices all play a role in breaches and exploits. But to reduce security to code alone misses the bigger picture. The modern threat landscape is multifaceted, involving people, processes, physical environments, and even cultural habits. For today’s security professionals, risk must be considered holistically, extending well beyond the lines of code.
Code Is Only One Piece of the Puzzle
Every line of code is a potential vulnerability, but even the most well-written software can be undone by weaknesses elsewhere. Consider a strong encryption algorithm rendered useless if passwords are stored on sticky notes in an office. Or a perfectly secure app that is compromised because of a misconfigured server or careless employee behavior. These examples highlight that while code matters, it cannot be treated as the sole factor in security planning.
Focusing too narrowly on technical vulnerabilities also creates blind spots. Attackers know that the easiest way in is often through human error or overlooked systems. By widening the scope of risk management, professionals can build more resilient defenses.
The Human Element in Security
Employees remain both the greatest asset and the greatest liability when it comes to protecting systems. Phishing campaigns, social engineering, and insider threats often bypass code altogether. A single click on a malicious link can undo months of careful coding and penetration testing.
Training, awareness, and accountability are essential in reducing these risks. Security professionals must think about how to empower employees with the knowledge to spot threats and the confidence to report them. Culture also plays a role: if staff feel pressured to work too quickly, they may cut corners on verification steps, inadvertently creating vulnerabilities.

Processes and Policies as Risk Factors
Organizations often underestimate the risks hidden within their own internal processes. For example, onboarding and offboarding procedures are critical to ensure employees do not retain access to systems after leaving. Similarly, lax policies around device usage or remote work can lead to uncontrolled exposure.
Security professionals must evaluate not just the technology stack but also the policies that govern it. This means creating and enforcing clear protocols for identity management, monitoring, and response. Without these safeguards, even the strongest code can be rendered ineffective.
Supply Chains and Third-Party Dependencies
Modern organizations rarely operate in isolation. They rely on cloud providers, software vendors, contractors, and supply chains. Each connection creates potential risk. If a third-party vendor suffers a breach, it can cascade into the organization’s own environment.
Security professionals need to evaluate suppliers with the same rigor they apply internally. This might include conducting risk assessments, requiring proof of compliance with standards, and maintaining visibility into how third parties handle sensitive data. Attacks through supply chains are increasing in sophistication, making this an area that cannot be overlooked.
Physical and Environmental Security
Digital threats dominate the conversation, but physical risks can be just as damaging. A server room with weak access controls, an office without proper surveillance, or unsecured portable devices can all lead to breaches. Even natural disasters and environmental hazards represent risks to critical systems.
Holistic security requires considering these physical factors alongside digital ones. Disaster recovery plans, redundant systems, and physical access controls are all part of a balanced strategy.
Ethical and Legal Considerations
Security is also influenced by ethical and legal obligations. Compliance frameworks like GDPR, HIPAA, or industry-specific standards exist to protect not only organizations but also the people they serve. A failure to adhere can result in severe financial and reputational damage, regardless of whether the code itself was secure.
Security professionals should stay aware of evolving regulations and ensure that their strategies account for both compliance and ethical responsibility. Trust is as important as technical strength in today’s interconnected world.
Insurance as a Safety Net
Even with comprehensive planning, no system is invulnerable. This is where safety nets come in. Cyber liability insurance, general business coverage, and other forms of risk transfer can provide crucial protection when the unexpected happens. The reality is that while professionals can mitigate most risks, they cannot eliminate all of them. Having the right insurance in place ensures that when breaches or incidents occur, the organization can recover more quickly and with less financial harm.
Security professionals should work hand in hand with business leaders to evaluate coverage options, such as those available from Next Insurance, which are tailored to modern business risks.
Building a Holistic Security Mindset
The main challenge for security professionals is adopting a mindset that views risk through a wide lens. It’s not enough to fix vulnerabilities at the code level; one must think about people, processes, supply chains, environments, and even cultural and ethical dimensions. This requires collaboration across departments, ongoing education, and proactive planning.
By embracing this holistic view, professionals can move beyond firefighting and instead create resilient systems that anticipate threats from every angle. Security is no longer just about preventing the next exploit; it’s about building trust, safeguarding people, and ensuring long-term stability.
Conclusion
Security is far more than code. While developers and analysts must continue to prioritize clean, secure software, the reality is that risk extends into every corner of an organization. Human behavior, processes, third-party relationships, physical safeguards, and compliance all play crucial roles. By acknowledging and preparing for these broader risks, security professionals strengthen their ability to protect not only technology but the entire organization.

-

 Legal6 days ago
Legal6 days agoMichigan man JD Vance sentenced to 2 years for threatening Trump and JD Vance
-

 Politics1 week ago
Politics1 week agoU.S. to designate Maduro-linked Cartel de los Soles as terrorist organization
-

 Health7 days ago
Health7 days agoCambodia reports fatal H5N1 bird flu case in 22-year-old man
-
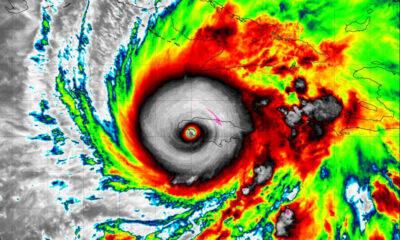
 World4 days ago
World4 days agoHurricane Melissa registered 252 mph wind gust, breaking global record
-

 Legal4 days ago
Legal4 days agoWoman in critical condition after being set on fire on Chicago train
-

 Politics7 days ago
Politics7 days agoEpstein survivors release PSA calling on Congress to release all files
-

 Legal4 days ago
Legal4 days ago1 dead, 2 injured in shooting at Dallas Walmart parking lot
-

 Legal3 days ago
Legal3 days agoSuspect in San Diego stabbing shot by authorities after fleeing into Mexico




